Introducing Cyber Security Lead Generation: Things You Should Know
Effective cyber security solutions are needed now more than ever as the…
Cybersecurity in Mobile App Development: A Must-Know for Business Owners
Mobile applications are considered to be one of the most important factors…
How Is AI Enhancing Cyber Security Solutions?
Artificial intelligence has significantly enhanced system operations and helped them to remain…
How Cyber Warfare is Transforming Global Security in the Digital Age?
In an era where digital limits are as significant as physical ones,…
7 Key Benefits of Emergency Fuel Delivery When Disaster Strikes
Disasters are only a few moments away. Massive storm damage or natural…
Top 10 Tips for Ensuring Online Privacy
Are you aware of the importance of online safety now? In today's…
How RPA Optimized Workflows in Cyber Security Operations
Has technology been a fortress or a battlefield for you in this…
What Is A Data Destruction Service, And Why Is It Important?
In the present-day virtual age, making sure the secure disposal of sensitive…
Polonez America: List of Prohibited Items for Sending to Poland from the USA
Knowing international shipping rules and constraints is essential for smooth and compliance…
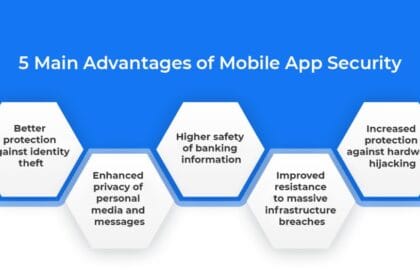
Security in Mobile App Development: Best Practices to Safeguard User Data
It sounds exciting to build a mobile app for your business. Today,…
Modern Cyber Security: Why Multi-Factor Authentication is Crucial
Multi-factor authentication, or MFA, is a key part of business security across…
Importance of Cybersecurity in Software Development
source Cybersecurity has turned out as one of the essential features of…