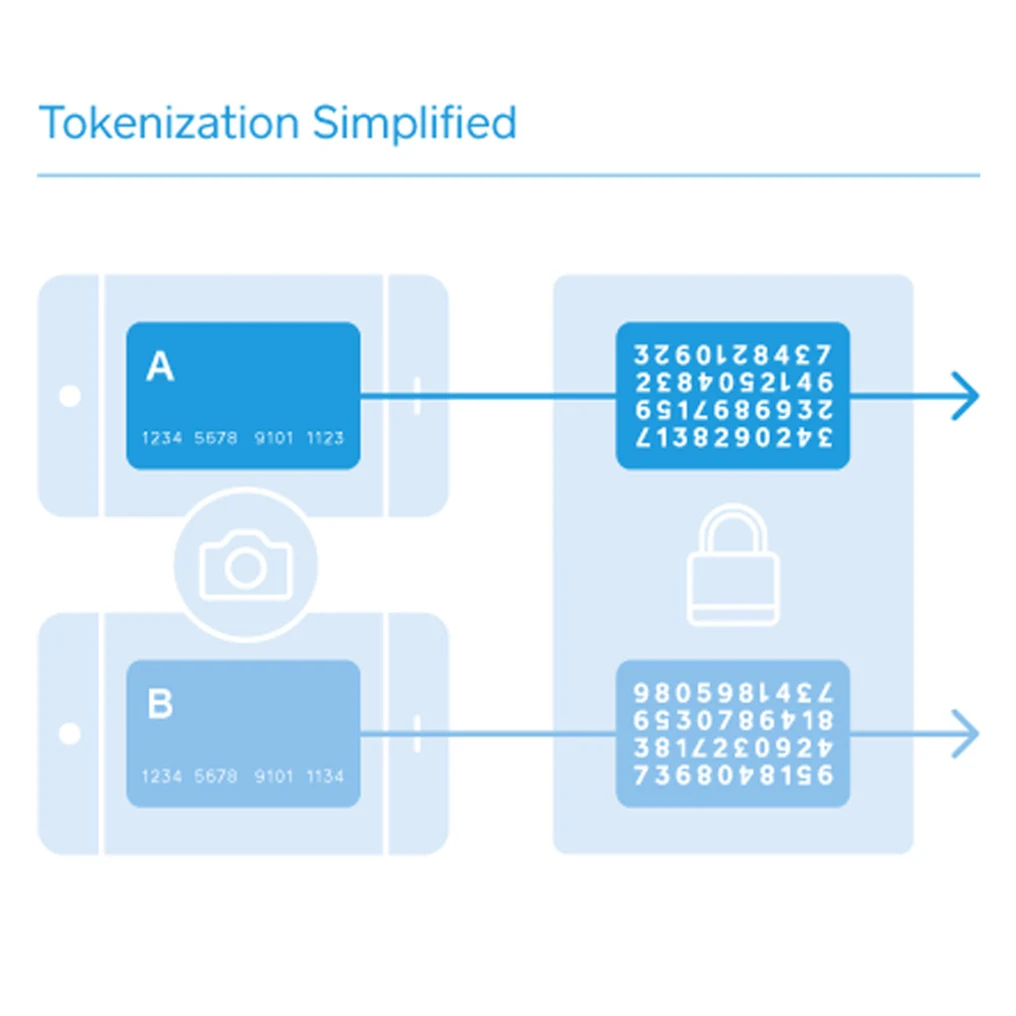
What Does Tokenization Mean?
It means a process of replacing original sensitive data elements with different…
Signs Of Poor Cybersecurity Practices And How To Improve Them
Source: Pixabay There have been a lot of discussions recently about the…
10 Essential Steps to Improve your Website Security
You must learn a few things about cybersecurity as a website owner.…
How to Hide Your IP Address?
Almost every second day, we are reading headlines about hackers hacking into…
Top Network Security Tools You Should Know About
Network security tools are software that monitors, protects and secures networks. They…
How to Keep Your Business Secure
Keeping a business secure is definitely one of the aspects of running…
5 Symptoms To Identify That Someone Is Trying To Break Your Cyber Security
We all know how cyberattacks are on the rise. It is important…
How to Protect Your Computer From Hackers and Cyber-Attacks
The internet is now integral to many aspects of our lives. As…
How to Protect Your Business from Cyber Attacks: Cyber Security Services
Business owners have a lot to worry about. Between hiring the right…
How Multi-Factor Authentication Works?
MFA requires that a user validate their identity by providing two or…
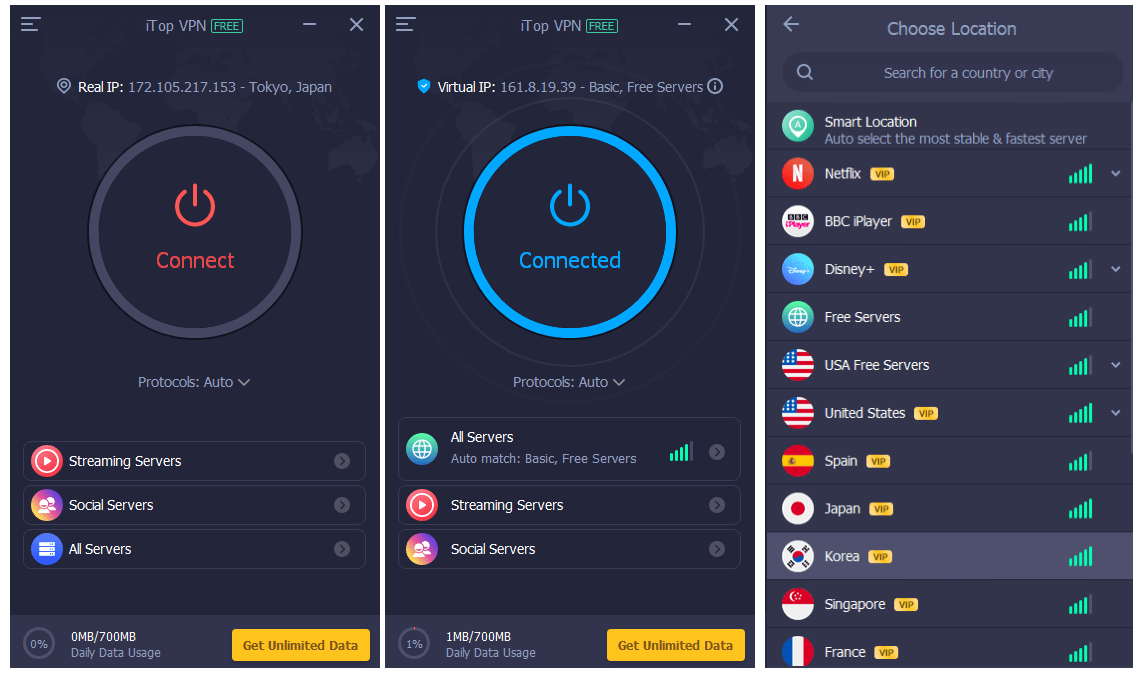
How to Safe Surf on the Web With iTop VPN?
So, with the rise of internet usage, a strong private connection is…