How to Efficiently Manage Your Passwords Online
You are not necessarily the most vulnerable person if a hacker or…
4 Rock-solid Tips to Strengthen the Security of Your Online Business
Image: Unsplash Statistics reveal that, in 2018, e-commerce retail sales worldwide accounted…
How VPN Browser Extension Can Keep You Safer Online
Cybersecurity and information confidentiality are in the news virtually daily. Every year…
Amazon Fire TV Stick VPNs: The Best Options
The Amazon Fire TV Stick is uniquely designed to convert any HDTV…
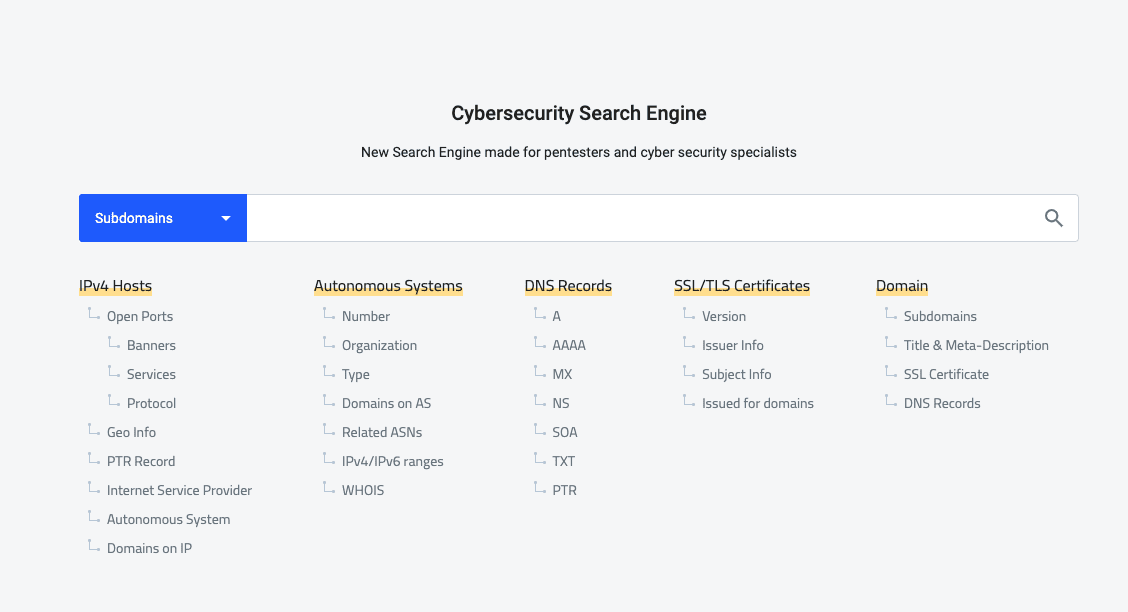
What is Spyse and How You Can Use It?
Most businesses and enterprises are now fully relying on web-based platforms. With…
How to Secure Your Business as Cybercrime Increases
Technology has completely changed the world around us over the last three…
Online Dating: Risks and How to Protect Your Privacy
With technology getting more and more advanced these days, anything is almost…
Learn How to Secure WordPress Login Page from Hackers
Change your WordPress login URL and cover up your wp-administrator to outmaneuver…
SME CyberSecurity is Everyone’s Job – Not Just IT
Swipe cards and CCTV are often used as the first defense of…
Why You Should Use a VPN While Torrenting
Should you use a VPN when torrenting? Torrent has a bad reputation…
How to Avoid Getting Your App Hacked?
In today’s modern world, the usage of mobile phones is increasing rapidly.…
How to Detect and Prevent Phishing Attacks?
A phishing attack could literally drain a business enterprise for millions and…